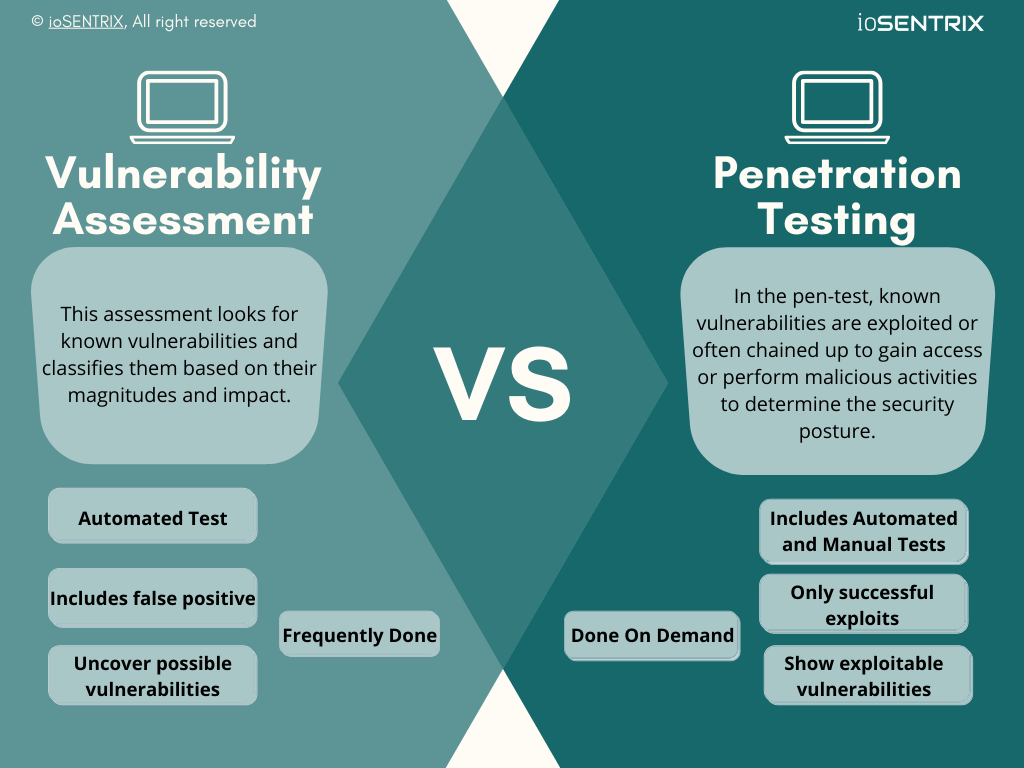
Scan For Penetration Testing . vulnerability scanning is a key component of your overall penetration testing processes. Maximize your penetration tests with tenable. In the context of web application security, penetration testing is commonly used to augment a web application firewall (waf). a penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. penetration testing uses manual scans and other methods to discover vulnerabilities and exploit them. a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. penetration testing, aka pen testing or ethical hacking, attempts to breach a system's security for the purpose of vulnerability.
from ceevxdlr.blob.core.windows.net
a penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. vulnerability scanning is a key component of your overall penetration testing processes. a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. Maximize your penetration tests with tenable. penetration testing, aka pen testing or ethical hacking, attempts to breach a system's security for the purpose of vulnerability. In the context of web application security, penetration testing is commonly used to augment a web application firewall (waf). penetration testing uses manual scans and other methods to discover vulnerabilities and exploit them.
Vulnerability Scanning Vs Testing at Rodney Whitmarsh blog
Scan For Penetration Testing In the context of web application security, penetration testing is commonly used to augment a web application firewall (waf). Maximize your penetration tests with tenable. a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. penetration testing uses manual scans and other methods to discover vulnerabilities and exploit them. penetration testing, aka pen testing or ethical hacking, attempts to breach a system's security for the purpose of vulnerability. a penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. In the context of web application security, penetration testing is commonly used to augment a web application firewall (waf). vulnerability scanning is a key component of your overall penetration testing processes.
From readdive.com
Application Testing Steps, Methods, & Tools Read Dive Scan For Penetration Testing vulnerability scanning is a key component of your overall penetration testing processes. penetration testing uses manual scans and other methods to discover vulnerabilities and exploit them. a penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. In the context of web application security, penetration. Scan For Penetration Testing.
From www.breachlock.com
Network Testing Fundamentals BreachLock Scan For Penetration Testing a penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. Maximize your penetration tests with tenable. In the context of web application security, penetration testing is commonly used to augment a web application firewall (waf). penetration testing uses manual scans and other methods to discover. Scan For Penetration Testing.
From blockfint.com
Test (Pentest) VS Vulnerability Assessment (VA Scan) Make Scan For Penetration Testing a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. penetration testing uses manual scans and other methods to discover vulnerabilities and exploit them. a penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for. Scan For Penetration Testing.
From www.bitlyft.com
Comparing Vulnerability Scanning and Testing Scan For Penetration Testing a penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. vulnerability scanning is a key component of your overall penetration testing processes.. Scan For Penetration Testing.
From www.hackersgarage.com
Testing Execution Standard Scan For Penetration Testing penetration testing uses manual scans and other methods to discover vulnerabilities and exploit them. In the context of web application security, penetration testing is commonly used to augment a web application firewall (waf). a penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. vulnerability. Scan For Penetration Testing.
From newcognito.com
Vulnerability Scan vs Test New Cognito Scan For Penetration Testing Maximize your penetration tests with tenable. a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. penetration testing uses manual scans and other methods to discover vulnerabilities and exploit them. vulnerability scanning is a key component of your overall penetration testing processes. a penetration. Scan For Penetration Testing.
From www.darasecurity.com
Test vs. Vulnerability Scan Dara Security Scan For Penetration Testing penetration testing uses manual scans and other methods to discover vulnerabilities and exploit them. vulnerability scanning is a key component of your overall penetration testing processes. a penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. penetration testing, aka pen testing or ethical. Scan For Penetration Testing.
From purplesec.us
What Are The Different Types Of Testing? Purplesec Scan For Penetration Testing a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. a penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. vulnerability scanning is a key component of your overall penetration testing processes.. Scan For Penetration Testing.
From www.prweb.com
The Defense Limited Company Launches SS7 Cloud Scanner SS7 Scan For Penetration Testing vulnerability scanning is a key component of your overall penetration testing processes. penetration testing uses manual scans and other methods to discover vulnerabilities and exploit them. Maximize your penetration tests with tenable. In the context of web application security, penetration testing is commonly used to augment a web application firewall (waf). a penetration test, also known as. Scan For Penetration Testing.
From telegra.ph
Online Test Telegraph Scan For Penetration Testing penetration testing uses manual scans and other methods to discover vulnerabilities and exploit them. vulnerability scanning is a key component of your overall penetration testing processes. penetration testing, aka pen testing or ethical hacking, attempts to breach a system's security for the purpose of vulnerability. Maximize your penetration tests with tenable. In the context of web application. Scan For Penetration Testing.
From securitywing.com
15 Testing ToolsOpen Source securitywing Scan For Penetration Testing a penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. Maximize your penetration tests with tenable. In the context of web application security, penetration testing is commonly used to augment a web application firewall (waf). penetration testing uses manual scans and other methods to discover. Scan For Penetration Testing.
From www.eccouncil.org
How to Find the Best Nmap Scan for Testing Initiatives Scan For Penetration Testing penetration testing, aka pen testing or ethical hacking, attempts to breach a system's security for the purpose of vulnerability. a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. Maximize your penetration tests with tenable. penetration testing uses manual scans and other methods to discover. Scan For Penetration Testing.
From www.emagined.com
Phases and Steps of a Test — CyberSecurity Services Scan For Penetration Testing penetration testing, aka pen testing or ethical hacking, attempts to breach a system's security for the purpose of vulnerability. penetration testing uses manual scans and other methods to discover vulnerabilities and exploit them. vulnerability scanning is a key component of your overall penetration testing processes. a penetration test, or pen test, is a security test that. Scan For Penetration Testing.
From geekflare.com
11 FREE Online Testing (Pentest) Tools to Test Application Scan For Penetration Testing a penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. Maximize your penetration tests with tenable. a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. penetration testing uses manual scans and. Scan For Penetration Testing.
From telegra.ph
Online Test Telegraph Scan For Penetration Testing Maximize your penetration tests with tenable. vulnerability scanning is a key component of your overall penetration testing processes. a penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. penetration testing uses manual scans and other methods to discover vulnerabilities and exploit them. a. Scan For Penetration Testing.
From networkassured.com
External Testing What to Know Before You Engage Scan For Penetration Testing penetration testing, aka pen testing or ethical hacking, attempts to breach a system's security for the purpose of vulnerability. a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. Maximize your penetration tests with tenable. a penetration test, also known as a pen test, is. Scan For Penetration Testing.
From www.simplilearn.com
What is Testing? A [StepbyStep] Guide Scan For Penetration Testing a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. penetration testing uses manual scans and other methods to discover vulnerabilities and exploit them. a penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for. Scan For Penetration Testing.
From theqalead.com
The Key Difference Between Vulnerability Scanning And Testing Scan For Penetration Testing In the context of web application security, penetration testing is commonly used to augment a web application firewall (waf). a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. Maximize your penetration tests with tenable. a penetration test, also known as a pen test, is a. Scan For Penetration Testing.